
Beware Phishers of Men: 5 Ways to Prevent Their Attacks and 5 Ways to Minimize the Damage After You’ve Been Hit.
At Enable, we are seeing an ever-increasing number of “phishing” schemes and other types of cyberattacks directed towards churches. For a variety of reasons, cybercriminals have identified churches as an attractive and potentially lucrative target. In this article we describe and analyze a recent church-focused phishing attack and provide 10 concrete steps you can take to protect yourself from these types of incidents and minimize any damage to your church in the event that you are targeted.
Anatomy of An Attack
After the church staff received word from a couple dozen members that they had received a suspicious message that appeared to be from their pastor, they were puzzled as to how so many members were included in the campaign.
Dozens of times our Enable team has run into the very email template that these members received. It is posted verbatim on various security sites and has been used by cybercriminals in both churches and businesses. Security experts call it a “CEO Spoof” because it often comes from an account that appears to be the CEO or another leader in the organization.
The first message in the campaign comes from a Gmail account that looks similar to the pastor’s real account – something like pastorname.churchname@gmail.com and it simply says that the pastor is working on something sensitive and asks if the recipient is available to help. The “bad actor” may send the message to several people or may target a specific staff person, often someone who appears to have purchasing responsibilities.
The first message in the campaign comes from a Gmail account that looks similar to the pastor’s real account – something like pastorname.churchname@gmail.com and it simply says that the pastor is working on something sensitive and asks if the recipient is available to help. The “bad actor” may send the message to several people or may target a specific staff person, often someone who appears to have purchasing responsibilities.
This is a common initial email to gain rapport and see who bites. Follow up emails will usually ask for money or gift cards.
This type of phishing attack is VERY common in churches because it’s so easy for attackers to get target emails, especially for staff people. Many churches list all their staff in a directory on their website, and include job descriptions, bios, and email addresses, etc. Key volunteers and lay leaders are often listed as well.
In a recent case we reviewed, however, the method the “bad actor” used to get access to a list of member emails was more advanced than what we’ve typically seen.
In many cases, we’ve seen the breach occur via “copy all” email messages, where the recipients are in the “CC” instead of the “BCC.” Someone who is CC’d on the messages from the pastor gets hacked, and the hacker uses the cc’d message to gain familiarity with the church and uses the list of recipients as targets for their attack.
In the recent case, however, we couldn’t initially figure out a common thread of who might have been CC’d on that email and who was getting the phish messages. It didn’t add up. This led us to ask the question – could the church’s church management software (“ChMS”) have been breached? If someone had access to the ChMS along with an account that had directory access, they could use that directory access to generate a list of targets.
We reached out to the ChMS and asked them to look for any suspicious logins. They took the request very seriously and did a good bit of investigation. Amongst their findings were several out-of-the-ordinary views of the directory by one of the church’s key volunteers. When we saw that email address, it didn’t look strange at all — formatted “username@onmail.com” in a way that matched what you might expect of a typical consumer email address.
We passed along the findings to the church staff thinking that the likely breach was a new “prospect” member who had more access than they should have. (This would be an easy way for a bad actor to gain access to a ChMS system and have whatever rights were available to a “prospect” or “guest” with access to the system.)
As the staff reviewed the information from the ChMS investigation, they made the connection. When they saw that specific email address, they remembered that they had recently received a request from a volunteer via the church’s “info@” email address to make a change to their record–from an old email address to a new email address. They then reached out to the volunteer and confirmed that the volunteer did not submit an address change request and that the address change request they received was indeed NOT authentic.
This volunteer’s name and role was published on the church website, making it possible for the attacker to use a known contact name when requesting an account change.
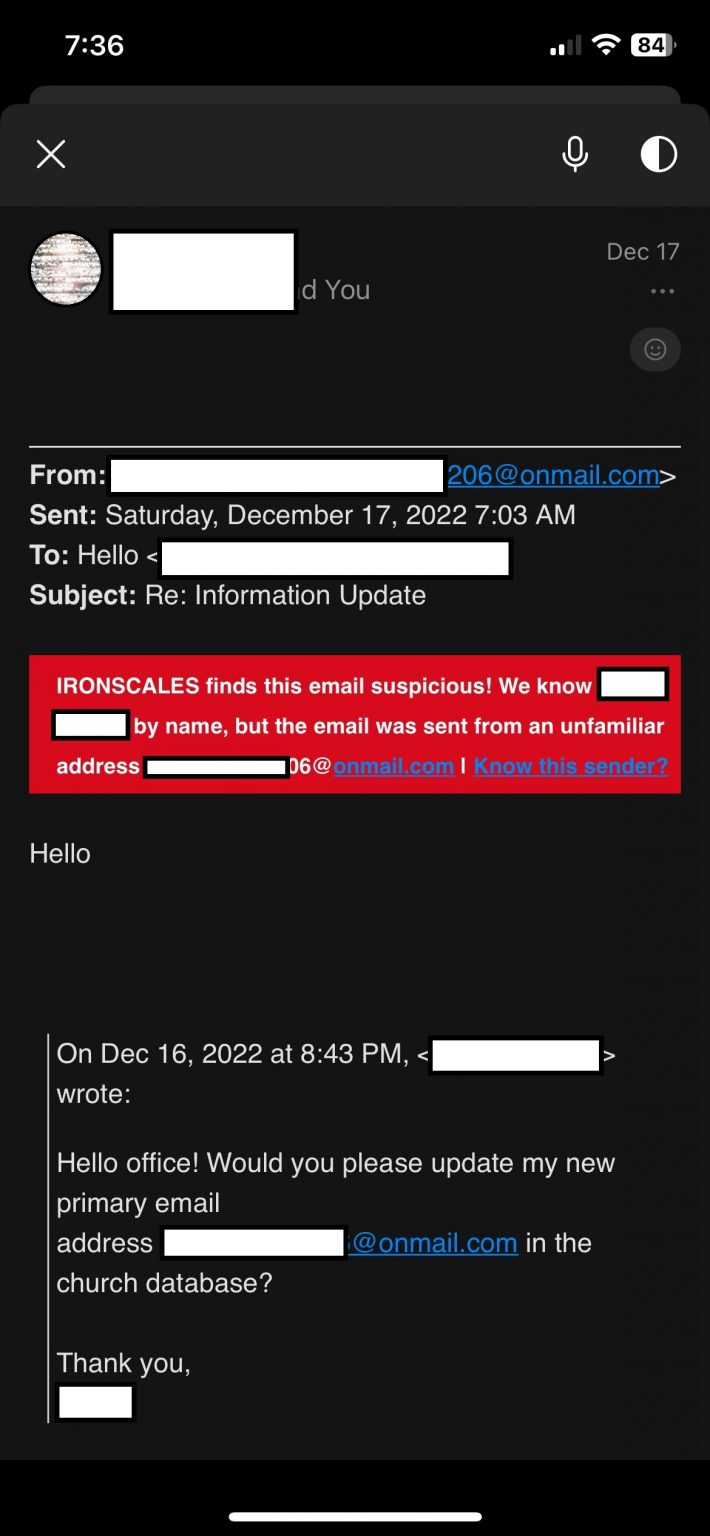
The message seems straightforward, but it does contain a couple of red flags.
- This is a key volunteer, and the request for change is sent to the general “info” link published on the church website, not an individual who they would commonly interact with.
- The message is unusually terse – “Hello Office.”
- Also, this church uses spoof detection software that did identify the message as suspicious.
What can be done to prevent this sort of thing?
- Anytime a change of contact request is received, verify it via a known good contact method, different from the method used to make the request. If you receive an email, verify via phone or text. If you receive a text message, verify via phone or email.
- Wherever possible, enforce Multi-factor Authentication (MFA). If MFA were enabled for the user, resetting her password would have required MFA to complete. Even though her username/email had been changed, the phisher had to reset the password prior to accessing the account.
- Reduce the information you publish on your website. In this case, the key volunteer was listed on the website, so the bad actor was able to use publicly available information to request contact information changes for someone who already had an account.
- When emailing groups of people, use your ChMS to send the message so that it doesn’t go out as a “CC” message. Limit information that you include in the message itself that could be used to give an attacker context for an attack, such as details of member prayer requests.
- If you need to send a group message through your work email client (such as Outlook or Gmail), use the BCC so that the recipients of the message are not easily identified.
What should we do if we experience an attack?
- Notify your senior leadership, such as an Executive Director or Business Administrator. You may need to involve other people, such as communications leaders early as well.
- Determine whether you have a breach. Is the issue a breach of church systems (ChMS, employee email accounts, etc.) or is the breach a recipient of a group email?
- If you have a breach, such as unauthorized access to your ChMS system, take steps to secure the system and lock out the offending account(s). Depending on the breach and how access has been obtained, you may need to take the system or server offline (but don’t turn it off).
- The best next step is to contact your Cyber Insurance carrier. They will have specific steps that they want you to take as follow-up. Depending on what information has been breached, they may involve legal counsel. It’s important that you don’t jump ahead of this step. You will need their counsel, because what you say and any steps you take after incurring such a breach may increase your risk. Your insurance carrier and legal counsel can help make sure that what you say and do is true and appropriately transparent without putting your church in a worse situation.
- Review how the attack occurred and adjust your processes. Do you need to better define roles and steps for verifying contact changes? Do you need to reduce permissions in your ChMS to limit who has access to the database? Should you reduce the information available publicly on your website? Do you need additional security awareness training for staff, leaders, and members?

